Hackers are wreaking havoc on cryptousers again, tricking them with a bit of social engineering and some ill-disposed tools disguised as useful, harmless software they can use in order to make things easier, when in fact is doing the opposite, taking their savings away and leaving them with an empty wallet, and a sense of despair. This time, hacker’s targets were IOTA users.
According to various reports from users, an estimated of $ 3.94 million worth of IOTA tokens were wiped out from numerous wallets. The cause of this thievery has to do with the way IOTA’s seeds are generated.
When a user wants to create a new IOTA wallet, he’s asked to come up with an 81-character seed that can be used to access it. Such seed can be generated offline. The problem is the way it can be created is not user-friendly, and may require a bit of knowledge from them in order to come up with a valid seed, such as creating a key via terminal (available on Mac or Linux, and on Windows with PowerShell, although this one is not recommended because of security reasons), or using an offline website named IPFS to do it by moving the mouse around to randomly come up with the letters.
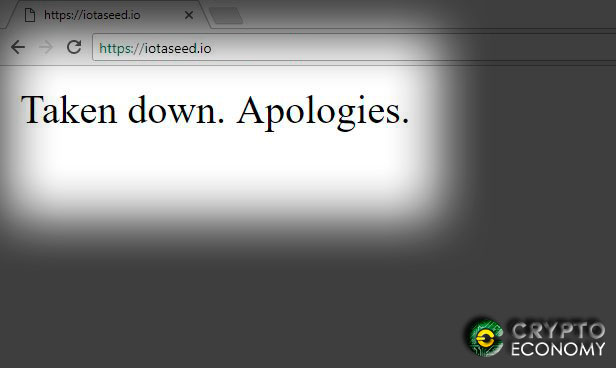
Because of this, some users turn to online seed generators, which are websites that easily create the seed for them. One of the most popular, iotaseed.io, had their servers under attack by hackers that were supposedly collecting seeds as they were generated, in order to use them and dry out wallets. At press time, the aforementioned site is down with a text message that reads “Taken down. Apologies.” This could mean all operations ceased for good after the dev team managed to regain control over the website.
On a side note, founder of Grand Centrix and member of the IOTA Evangelist Network Ralf Rottman wrote a post about how the attackers launched a Distributed Denial of Service (DDoS) attack against several of IOTA’s full nodes, thus preventing users from recovering their money. He remarks that affected nodes were those run by the community, as his company’s privately-run nodes were all the time safe and sound.
He also explained that because of scenarios like this, he and the IOTA Foundation always warn their users against using online seed generators. “Generating an IOTA seed in a secure, completely offline fashion is the best protection you can get,” he said.
Although the IOTA Foundation is reportedly developing a more user-friendly wallet that can simplify the security process, those who have lost their funds as a result of this attack have little to no hope of recovering them.