NIX is committed to privacy since they believe that each user is free to choose to have it or not. To do so, the platform uses its Ghost Protocol which is continuously updated and improved by the NIX team. This protocol combined with Atomic Swaps is what the NIX team wants to offer the world: transfers between anonymous and decentralized chains.
Privacy in transactions could basically be divided into 2 points: point 1 would hide the identity of the issuer, point 2 would hide the identity of the transfer recipient so that tracking them is impossible.
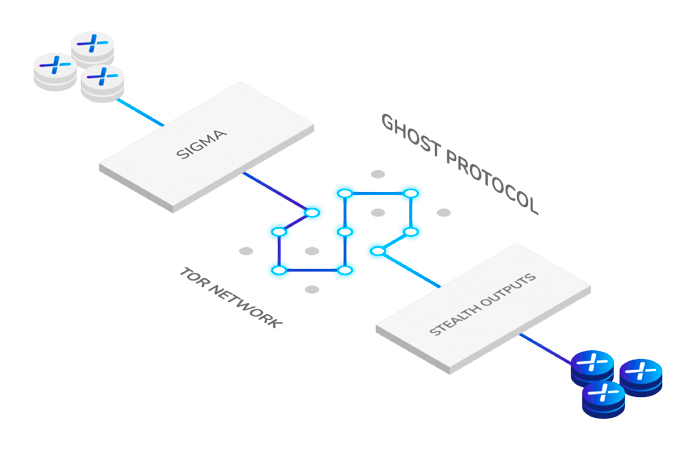
The Ghost Protocol of NIX
The NIX Ghost Protocol consists of several privacy components. Initially, the platform enabled Zerocoin with hidden exits combined with Tor networks, eliminating the possibility of detecting the place of the initial transaction.
In September 2018, the platform launched the Ghost Protocol to its mainnet along with the Ghost Vault and the upgrade from PoW to PoS.
At present, the Ghost Protocol is formed by a set of sub-protocols that include Sigma – which replaced Zerocoin – commitment key packs, Tor and Dandelion++.
Ghost Vault
Based on the Ghost Protocol, NIX developed its Ghost Vault, which allows transfers to the vault and from there to send them to other NIX addresses without leaving any trace, also, the coins stored in it will remain private.
The process of sending NIX to the vault is called “ghosting” and the process of sending cryptocurrencies from the vault to another address is called “unghosting”. You can see a guide of the process by clicking this link of the NIX wiki.
SIGMA
In June 2019, upon reaching block 232000, NIX became the first network to implement SIGMA on its Mainnet, which brings scalability and a new level of privacy to the network.
Sigma reduces the chain size by 94% and eliminates the necessary trust configuration with Zerocoin, which significantly increases scalability and the level of anonymity. This makes NIX a great competitor against privacy-focused projects.
With zero-knowledge-proof elements to hide transactions and data movements along with the Zerocoin Protocol and Commitment Key Packs scheme, the NIX privacy protocol is the most robust and mathematically secure cryptocurrency system.
Says the Whitepaper 2.0 from NIX platform.
Ghostnodes
https://www.youtube.com/watch?v=WAXeUOAgEAo
To carry out this entire process, NIX uses Ghostnodes, any smart contract that requires autonomous privacy is processed in them.
To maintain and operate these Ghostnodes, one must own 40,000 NIX, keeping this amount in a non-standard “G” address and proceeding to the configuration of the Ghostnode. Its main purpose in the network is to process the Ghost Protocol transactions.
This activity will be rewarded with 0.25% of each transaction and a partial reward that is around 70% of the block, which is equivalent to 8.448 NIX each time a new block is generated.
The future of NIX
The ultimate goal of the NIX project is to offer its users complete privacy and decentralization, and although they have other projects fighting in this sector, such as Monero, or the newcomers Beam or Grin, the team behind them does not stop working to reach their set goals.
In addition to offering total privacy, NIX works in another of its assets to become a successful project, its decentralized exchange manager (DEX), thanks to which users can make transactions between DEX in an easy and fully private way.